强壮逆向人!
好好学逆向
moectf题真的好,每日一题
2025.6.19 考完试一定写🥲
2025.7.19 会写的会写的😫
A_game
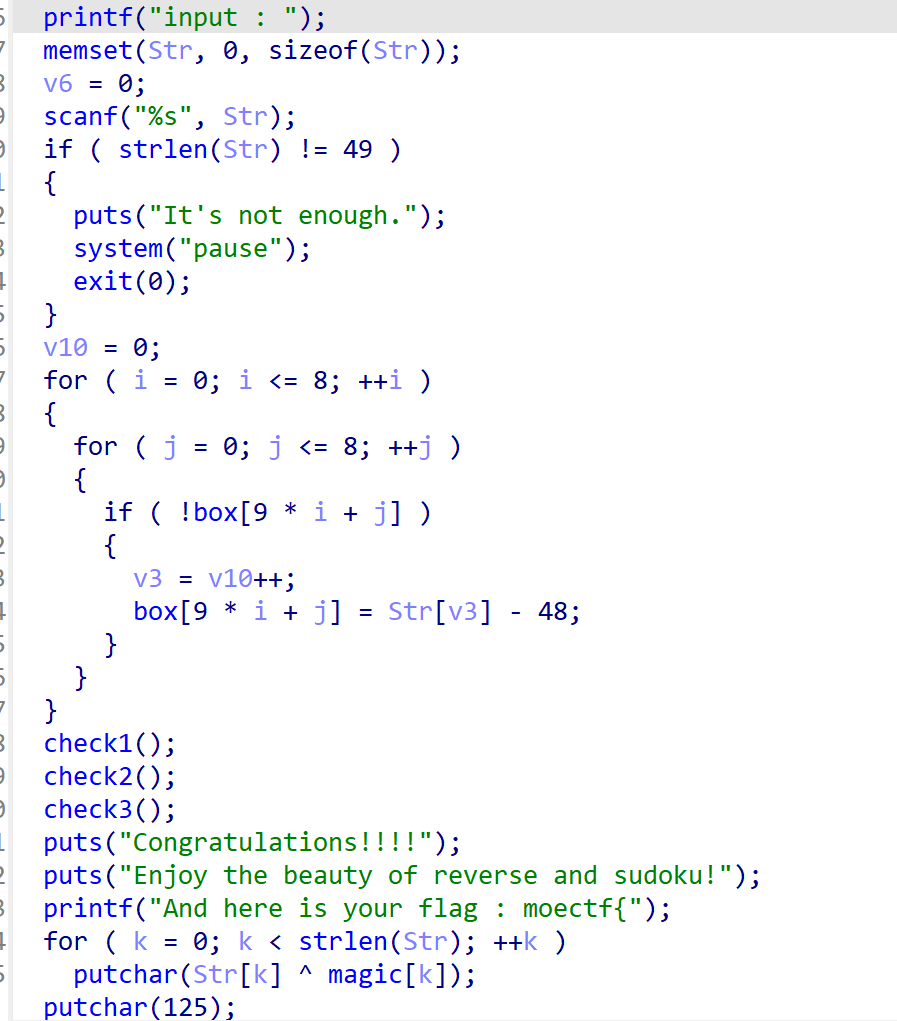
好清晰的逻辑,好清晰的函数名🥲 首先输入49个字符的字符串,将这49个字符填入9x9的box数组中值为0的位置,经过3个check函数验证是否正确,如果正确,那么将str与magic数组异或得到flag
接下来我们查看check1函数的代码
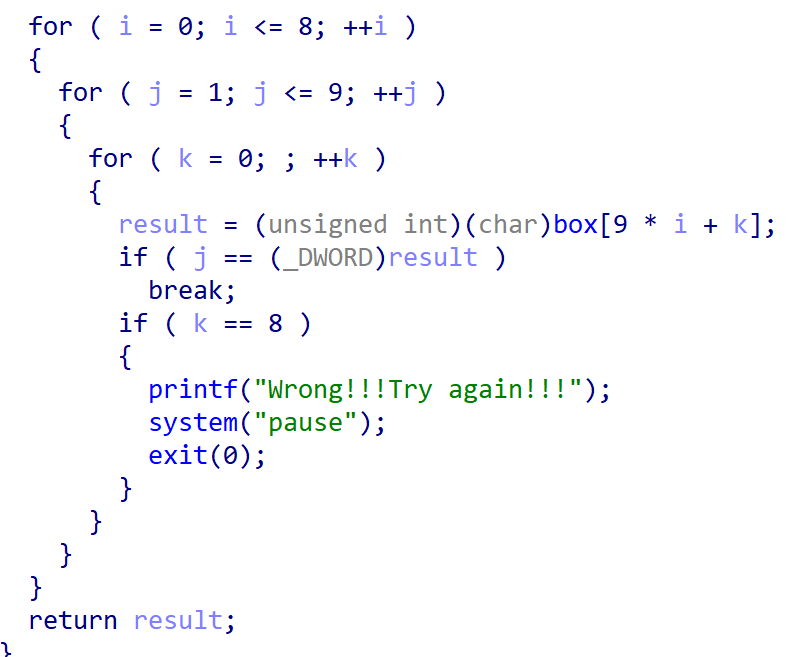
每一行必须包含数字 1~9,不能重复,也不能缺少
check2函数:每一列必须包含数字 1~9,不能重复,也不能缺少
check3函数:每一个 3x3 小宫格中都包含 1~9 各一次
很明显,这是数独游戏的规则,我们需要填入正确的49个数字
直接用python脚本
1 | from typing import List |
Android_Cracker
用jadx打开找到MainActivity打开就是了
Broken_hash
没做出来,复现一下
有一个师傅的解法很简单:
这个程序需要输入88位字符,经过变种SHA1算法转化,再和一个数组比较
先输入88个a,下断点动调
看到了加密后的数组,发现a变成0x0D7C1A410
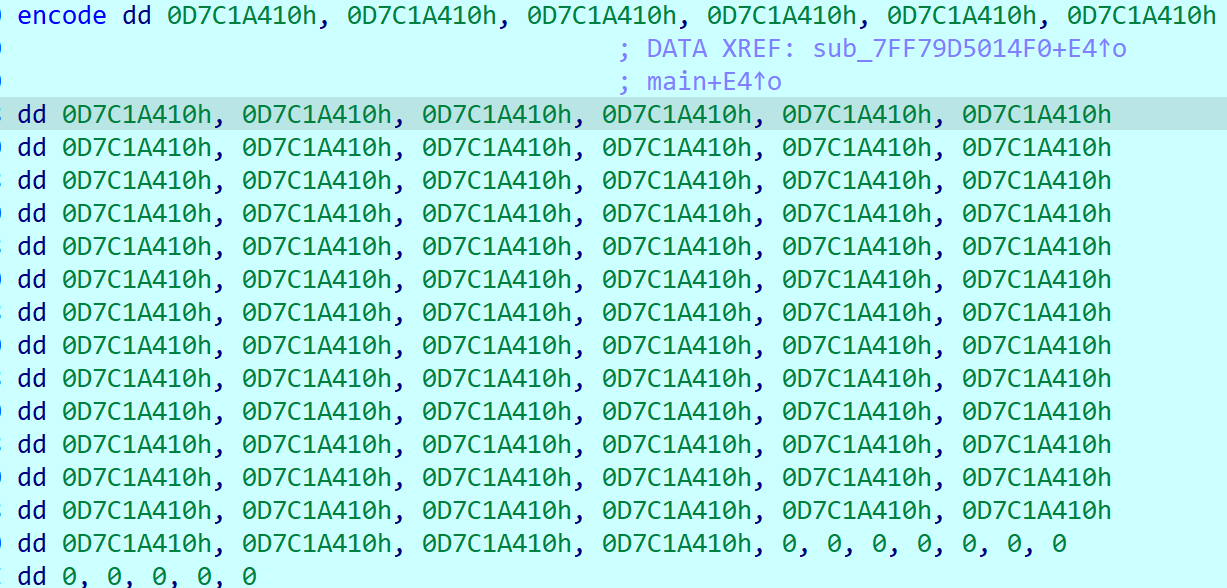
所以可以输入abcdefghijklmnopqrstuvwxyz1234567890_!ABCDEFGHIJKLMNOPQRSTUVWXYZ{}aaaaaaaaaaaaaaaaaaaaaa
建立一个映射表
1 | a = [0x64744C9A, 0x047C2FF1, 0xA2D74292, 0x85BEF77E, 0x711FCBF7, 0x669E1609, 0x6BBD9DB6, 0x6941C8A4, 0xB16E48B3, 0xDE321186, 0x5251E8C2, 0xFB8F95A7, 0x711FCBF7, 0xCB5C3FAD, 0x36568AF5, 0xFB8F95A7, 0x82ACF96A, 0x75DCD570, 0x7EF00E40, 0xFB8F95A7, 0x4BE9314A, 0xCB5C3FAD, 0xA2D74292, 0xDE321186, 0xFB8F95A7, 0x46927FA8, 0xB16E48B3, 0xD7C1A410, 0x567375C3, 0x711FCBF7, 0xFB8F95A7, 0x9C19F0F3, 0xD035E914, 0xFB8F95A7, 0x6941C8A4, 0x0B7D1395, 0xD7C1A410, 0xC87A7C7E, 0xFB8F95A7, 0xD7C1A410, 0xDE321186, 0x5251E8C2, 0xFB8F95A7, 0xD5380C52, 0xBEA99D3B, 0xCEDB7952, 0xFB8F95A7, 0x73456320, |
官方wp:考察SEH,patch程序,以及编写交互脚本
本题使用了一个哈希算法(SHA1,魔改了部分参数)对flag每一位计算哈希,然后跟密文对比验证。当然,只取了最终哈希值的前4个字节(防止直接用SHA1去查彩虹表)。 预期解法是去patch程序输出,让程序能够输出check过的长度(即for循环中的i)。具体而言,这个循环是每次验证一位,不正确就退出循环,所以当我们的输入只有前3个字符正确的时候,i退出时应该是3;前4个字符正确的时候,i退出时应该是4。我们想办法让程序输出这个i,然后每一位去尝试每一个可见字符。i每自增一次,我们就知道当前这一位字符是正确的。当然了,这道题使用异常处理隐藏了真正的输出,真正的输出字符附在密文的最后,进行了一个异或0xff的解密之后才输出。,且加了反调试,如果是在调试状态下,不会进入异常,会进入假的print。
SEH异常处理机制
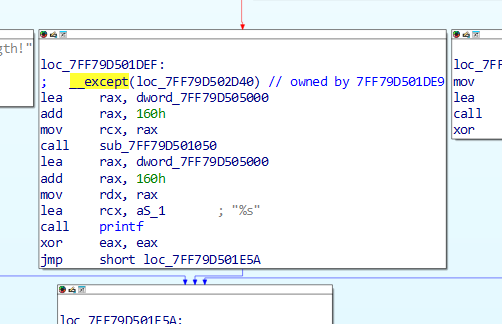
找到了异常处理函数,这个函数作用是打印flag,patch一下
还没成功,再研究一下



