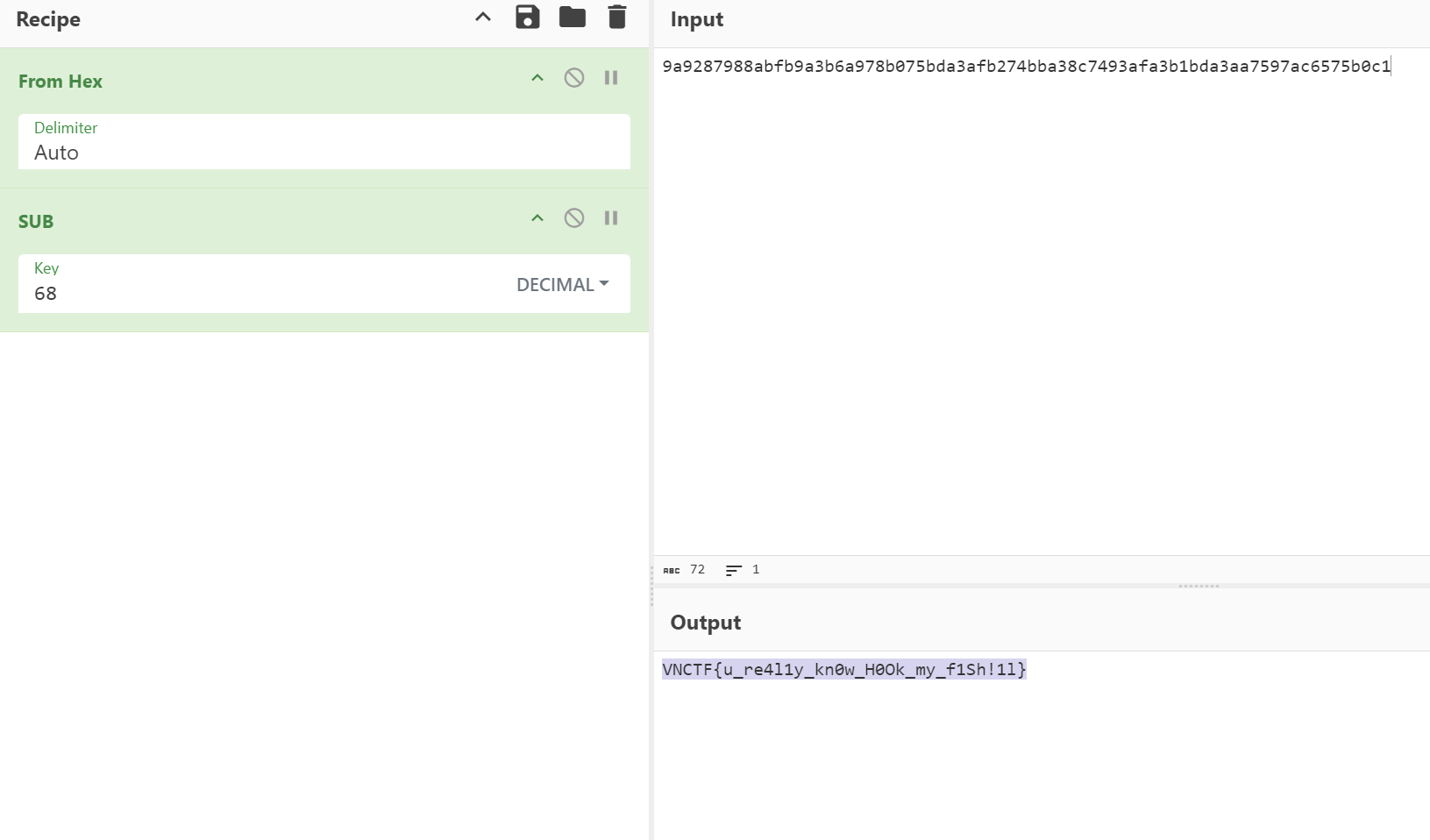
😫今天终于想起来复现了,这次比赛没做出来一道题,好惨
hook_fish
分析过程
总之就是输入flag验证是否正确
先找到主函数
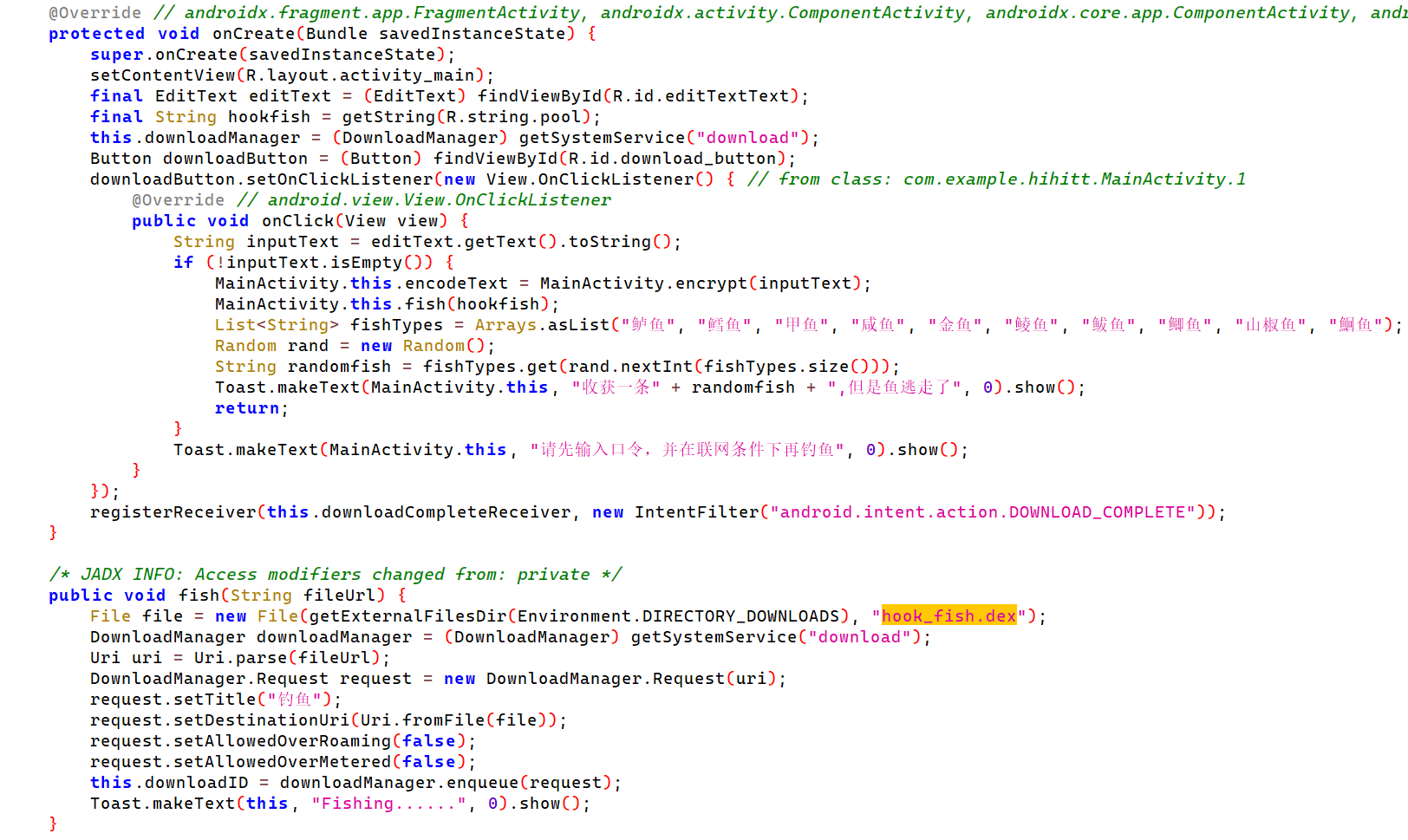
check验证函数应该在hook_fish.dex中,根据fish函数的参数hookfish找到下载链接
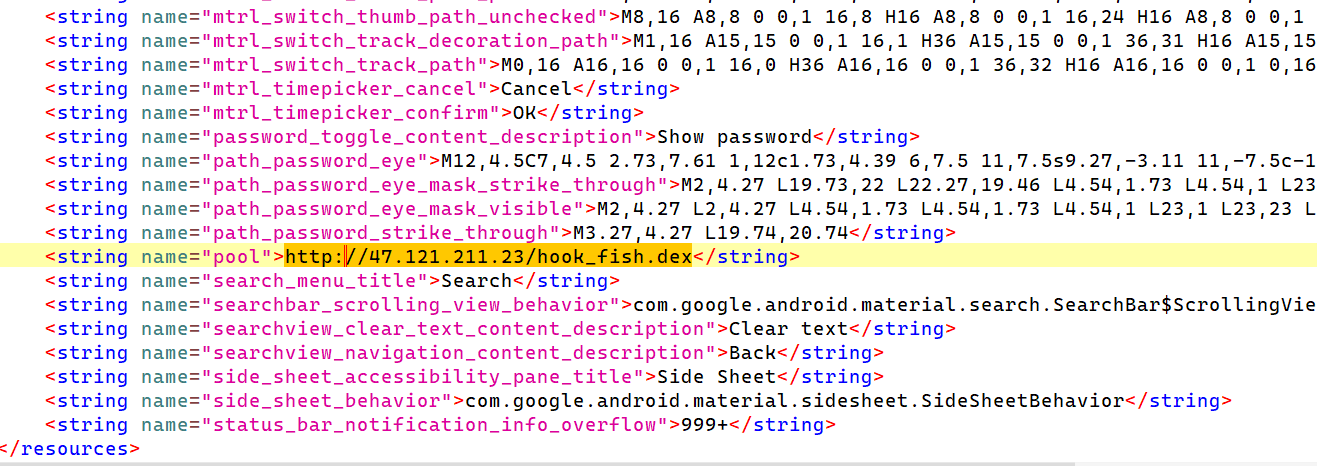
输入的flag先经过本地encrypt函数加密,再经过hook_fish.dex中的check方法进行混淆
解密过程
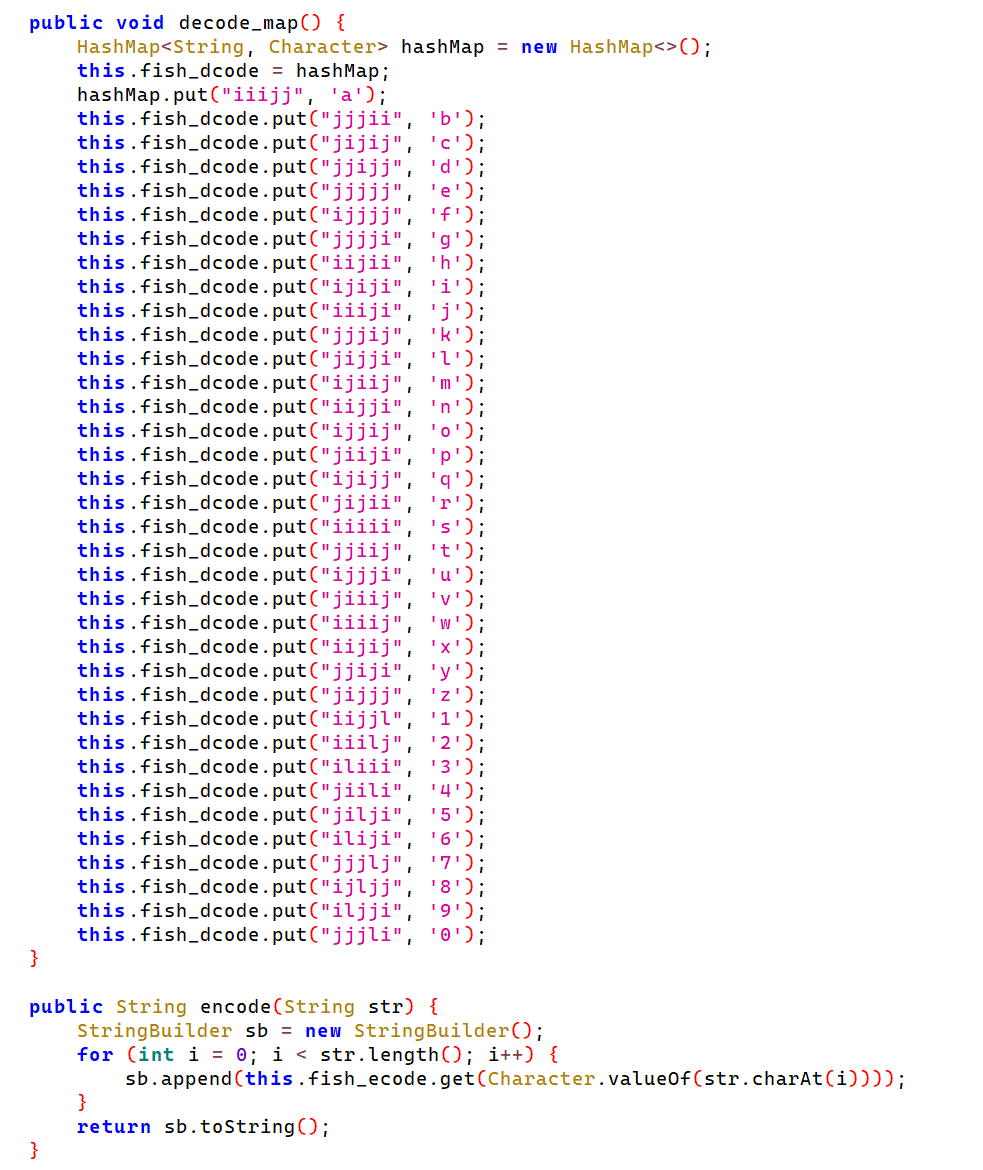
check方法用哈希映射加密,在mainactivity中保留了decode方法,可以用hook方法解密
1
2
3
4
5
6
7
8
9
10
11
12
| Java.perform(function() {
var MainActivity =
Java.use("com.example.hihitt.MainActivity");
console.log("找到类: com.example.hihitt.MainActivity");
MainActivity.fish_fade.implementation = function() {
console.log("阻止删除了文件");
var result =
this.decode("jjjliijijjjjjijiiiiijijiijjiijijjjiiiiijjjjliiijijjjjljjiilijijiiiiiljiijjiiliiiiiiiiiiiljiijijiliiiijjijijjijijijijiilijiijiiiiiijiljijiilijijiiiijjljjjljiliiijjjijiiiljijjijiiiiiiijjliiiljjijiiiliiiiiiljjiijiijiijijijjiijjiijjjijjjljiliiijijiiiijjliijiijiiliiliiiiiiljiijjiiliiijjjliiijjljjiijiiiijiijjiijijjjiiliiliiijiijijijiijijiiijjjiijjijiiiljiijiijilji");
console.log("解密结果: " + result);
};
});
|
得到解密结果: 0qksrtuw0x74r2n3s2x3ooi4ps54r173k2os12r32pmqnu73r1h432n301twnq43prruo2h5
然后逆向解密
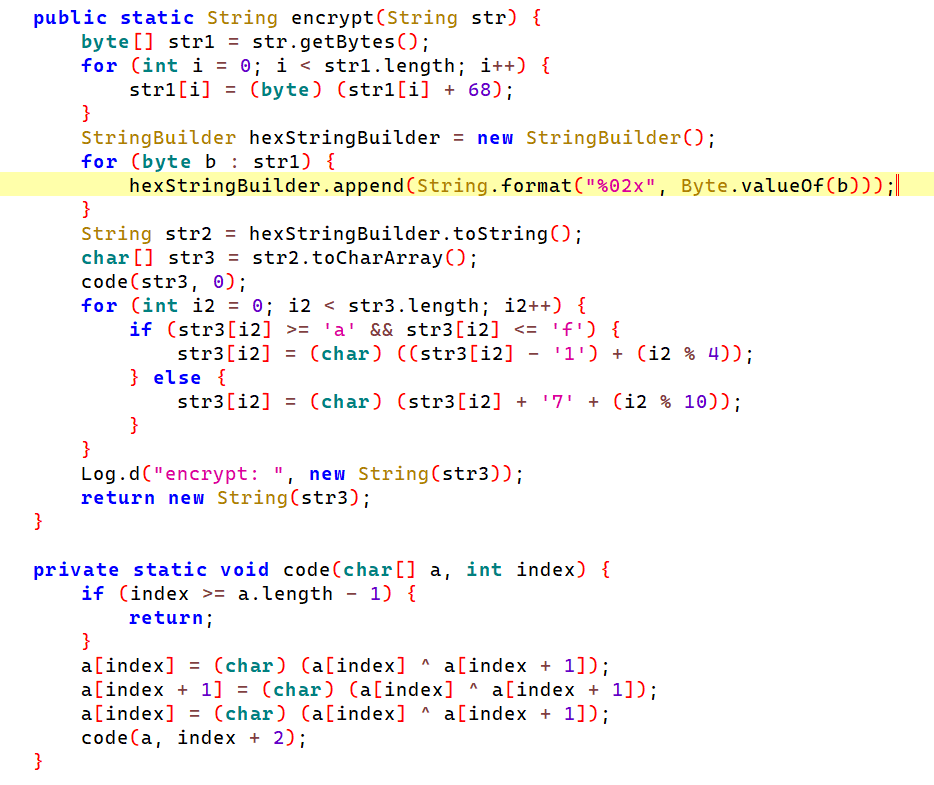
code函数的作用就是每两个字节之间交换顺序
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| #include <stdio.h>
int main(){
unsigned char encode[73] =
"0qksrtuw0x74r2n3s2x3ooi4ps54r173k2os12r32pmqnu73r1h432n301twnq43prruo2h5";
for(int i =0;i<72;i++){
if(encode[i] >='0' && encode[i]<='9'){
encode[i]= (encode[i]-(i%4))+49;
}else{
encode[i]= (encode[i]-(i%10))- 55;
}
}
for(int i=0;i<72;i+=2){
char tmp = encode[i];
encode[i]=encode[i+1];
encode[i+1]=tmp;
}
for(int i=0;i<72;i++){
printf("%c",encode[i]);
}
}
|